Monday, October 24, 2011
105. Facebook Hacking in BT5
BackTrack is a Linux-based penetration testing arsenal that aids security professionals in the ability to perform assessments in a purely native environment dedicated to hacking. Regardless if you’re making BackTrack your primary operating system, booting from a LiveDVD, or using your favorite thumbdrive, BackTrack has been customized down to every package, kernel configuration, script and patch solely for the purpose of the penetration tester.
Friday, October 14, 2011
104. How To Convert a SIM to a MicroSIM with a Meat Cleaver
 Everything I describe below applies to the iPad, iPad 2 and iPhone.
Everything I describe below applies to the iPad, iPad 2 and iPhone.This morning, my shiny new iPad 3G 64Gb arrived from the USA! The only problem was, it had an AT&T MicroSIM and as yet there is no such thing in the UK.
So what’s the solution? Get a chopping board, a meat cleaver and a pair of scissors – simples!
Apologies for the focus issues with my new Canon IXUS 210 – it is going back today!
Saturday, July 30, 2011
Thursday, July 28, 2011
102. Install Android 2.3 on HTC Wildfire
Sometime ago I got an HTC Wildfire and was having loads of fun using it, but every time I wanted to do anything more "creative" i was stopped by the binded nature of phone, hence i decided to root it (jailbreak it apple fellas) and get complete control over my device. Here, I am covering step by step guide to root HTC wildfire 2.2.1 and install Android 2.3 on HTC Wildfire. To do the rooting you must have your Wildfire with S-OFF, HBOOT 1.02.0002 and Android 2.2.1 . You can check it by booting into HBOOT (power on your phone by holding the VOLUME DOWN + POWER button) .This method is strictly for the 2.2.1 owners. How you can turn the S-OFF is your headache, you can try the alpharev (ask the team if they can get you a 2.0 test version...) or you can wait for Unrevoked 3.33 or you can straight off go to market and hunt for XTC clip. Either way, try it and don't attempt to anything before you get S-OFF. Actually the notorious S-ON flag is the cause rooting wildfire is such a pain in the a**.
101. Create A Zip Bomb
A zip bomb, also known as a Zip of Death, is a malicious archive file designed to crash or render useless the program or
 system reading it. It is often used byvirus writers to disable antivirus software, so that a more traditional virus sent afterwards could get into system undetected. A zip bomb is usually a small file (up to a few hundred kilobytes) for ease of transport and to avoid suspicion. However, when the file is unpacked its contents are more than the system can handle.You can make your own zip bomb to annoy your friends or just out of curiosity (or wilderness) to experiment with it. Make sure you don't detonate it on yourself.
system reading it. It is often used byvirus writers to disable antivirus software, so that a more traditional virus sent afterwards could get into system undetected. A zip bomb is usually a small file (up to a few hundred kilobytes) for ease of transport and to avoid suspicion. However, when the file is unpacked its contents are more than the system can handle.You can make your own zip bomb to annoy your friends or just out of curiosity (or wilderness) to experiment with it. Make sure you don't detonate it on yourself.Wednesday, July 27, 2011
Tuesday, July 26, 2011
98. USB flash drive portable browser
 Have you ever been some place other than your home on your computer? If your answer is anything other then yes, you need to stop being a computer hugging hippy and go outside, get a whif of some fresh air, step on some dog crap and accidently run over a cat. It’ll do you some good. Anyways, have you visited someone somewhere and while using his/her/its computer, you realized you didn’t know a password because it was saved on your browser, or you wanted to show your friend that one cool website with the non-Asian ninjas, but it was in your bookmarks, or you wanted to use an extension you had installed on your browser that got rid of homosexual ads? Well you can. It’s called portable browsers, a.k.a a browser on your USB drive.
Have you ever been some place other than your home on your computer? If your answer is anything other then yes, you need to stop being a computer hugging hippy and go outside, get a whif of some fresh air, step on some dog crap and accidently run over a cat. It’ll do you some good. Anyways, have you visited someone somewhere and while using his/her/its computer, you realized you didn’t know a password because it was saved on your browser, or you wanted to show your friend that one cool website with the non-Asian ninjas, but it was in your bookmarks, or you wanted to use an extension you had installed on your browser that got rid of homosexual ads? Well you can. It’s called portable browsers, a.k.a a browser on your USB drive.Monday, July 25, 2011
Sunday, July 24, 2011
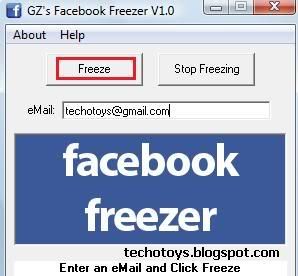
93. Facebook Account Freezer
Facebook Freezer selects random login id and password combination to login to victim account. Due to wrong login attempts, Facebook temporarily bans the victim from logging in to his account. But, if Facebook Freezer is allowed to run on computer for a long time, Facebook bans victim from logging in to his account as long as Freezer is running. Thus, inspite of correct login id and password, victim is unable to login to his Facebook account. Thus, we are able to hack Facebook account using Facebook Freezer.
91. Convert Your RAM into Graphic Card
Many times we are stuck up with a system that just doesn’t provide enough juice to run the latest game…the result being you either spend a pot of money (atleast Rupees 3500 or 70$) for getting the latest graphics cardor you just read reviews of games like Crysis , Far Cry on gamespot and feel like a noob,fully knowing that your system just won’t be able to support it....
Thursday, July 14, 2011
90. Break The Database of a Website Using SQL injection
 In this tutorial i am going to guide how to hack the website database using SQL injection. First of all you need to understand what is sql injection, so kindly read this tutorial
In this tutorial i am going to guide how to hack the website database using SQL injection. First of all you need to understand what is sql injection, so kindly read this tutorial89. Virus Codes to Disable All hard disks
Hi friends,here i give you give the C++ virus code. Actually Batch code is converted to C++ virus code. If you like you can use it as batch code also.
Sunday, July 10, 2011
88. View Passwords Behind Asterisk
Today I am going to tell you a really cool trick which you can perform using Javascript. This trick will allow you to view passwords behind Asterisk.You can use this trick on any web page which contains password hidden behind Asterisk.
Saturday, July 9, 2011
87. Create Keylogger in C++
Hi friends, the most interesting part of the hacking is spying. Today i am going to introduce to the C++ Spyware code. It is going to be very fun. You can install this spyware in your college/school or in your friend system, and get their username and passwords. This is very simple hacking trick when compared to phishing web page.
86. Hacking Autorun.inf Virus Attacks
When i studied second year(diploma), my friends told that autorun.inf is virus. I thought so. Because my antivirus blocks autorun.inf files. In third year when i search about autorun.inf file in net, i realize about the auto run file.
Today i bring some files from my college system. When i insert the pen drive in my system, there are lot of exe files.They are viruses. I delete all of them. Finally i opened the autorun.inf file in notepad and saw the instructions. Then only i remembered that i forget to post about autorun file. This article will give you complete details about the autorun.inf file.
This is the instructions that saved in the infected(call virus programs) autorun.inf file:
85. How to block or Disable Autorun.inf file in windows
 Depending on the version of Windows that you are using, there are different updates that you must have installed to correctly disable the Autorun functionality:
Depending on the version of Windows that you are using, there are different updates that you must have installed to correctly disable the Autorun functionality:To disable the Autorun functionality in Windows XP, in Windows Server 2003, or in Windows 2000, you must have security update 950582, update 967715, or update 953252 installed.
Saturday, June 4, 2011
84. Hack Or Reset Windows Password In 5 Easy Steps
 It happens often, we leave our beloved pc in our home and go for a vacation, and after coming back we forget the admin password for it to enter. And your so loved PC turns against you by not letting you enter. The scenario can be anything but the problem is frustrating and same for all.
It happens often, we leave our beloved pc in our home and go for a vacation, and after coming back we forget the admin password for it to enter. And your so loved PC turns against you by not letting you enter. The scenario can be anything but the problem is frustrating and same for all.Today, we will discuss how to get away with even after you forget your Windows (XP, 2003, ME, Vista, Win7) administrator password. However we will discuss about the small tool that will help us in getting the work done. We are not going in details on how this works and keep it for a future post.
Wednesday, May 25, 2011
80. Open Docx Files without Microsoft office 2007
79. How to create your own Customized Run Commands
This post will help you in creating your own customized Run command that you can use to initiate a variety of programs. The Run is a special in built utility that allows you to interact with the system through the command line. There are several in built commands to initiate a variety of programs like calc for Calculator, cmd for Command Prompt. So let’s start out and create our own command.
Wednesday, March 30, 2011
78. Backup your Linux machine with LuckyBackup
LuckyBackup is an Open source software developed under GPL license. It’s main purpose is to keep your important folders in sync with the backup folders so that you can always have a backup copy of your important files and folders ready.
77. Load and use multiple OSs from your USB drive
Ever felt like carrying your Ubuntu, Fedora, Tiny-core and all other OS’s iso in your pen drive? Yes, you can now carry all your favorite Operating systems with you wherever you go and boot from them using the same USB drive.MultiBoot USB is a freeware which can help you to use the multiple OS iso files on the same pen drive.
Sunday, March 20, 2011
74. How to Operate Mouse Pointer Without Mouse
You have Mouse problem ??
I will give you suggestion
Press Left Alt + Left Shift + Num Lock Button + Ok
I will give you suggestion
Press Left Alt + Left Shift + Num Lock Button + Ok
72. How To Hide Text In Images (Steganography)
It is widely claimed that the trick of hiding text into images (Steganography) has been used by Al Qaeda for communication for carrying out 911 attacks.Well if you also want such a strong security in your communication so that nobody else can interpret your messages except the desired person then we have a free solution for you.
By using this trick your text will get hidden into any image of your choice without increasing its size or without reducing its quality.Your data will be encrypted in the image with RC_4 encryption plus SHA hashing.So ,there is no need to worry that it can be easily cracked by anybody.
71. Trick on How To Enable Right Click on Websites
 You probably may have come across some websites that doesn’t allow you to copy any content from there websites by blocking right click.When you press right click on these websites either you will get a prompt with some message or nothing will happen.Sometimes this is very annoying as you may need that content for your college project or some other urgent purpose.There are several workarounds to bypass this.
You probably may have come across some websites that doesn’t allow you to copy any content from there websites by blocking right click.When you press right click on these websites either you will get a prompt with some message or nothing will happen.Sometimes this is very annoying as you may need that content for your college project or some other urgent purpose.There are several workarounds to bypass this.I will tell you the best and the most simple trick.You don’t require any software or addon for this trick.Website that block the right click do it using a javascript code.If you block javascript code in your browser then your right click cannot be blocked. Here is the tutorial on How To Enable Right Click on Websites
69. How To Watch 18+ Videos on YouTube Without Logging In
Youtube is the most popular video streaming website. YouTube has thousands of streaming videos on nearly every topic. Which are free to watch.Certain videos that contain nudity, explicit, or violence content are put under 18+ category and you can’t watch these videos on YouTube unless you are logged into your YouTube / Google account. In this post I will show you a simple hack on how to see those videos
Wednesday, February 23, 2011
Tuesday, February 8, 2011
65. Batch VIRUS Killing “ NORTON, LIMEWIRE, EXPLORER, MSN
It will
1) Copy itself into startup
2) Copy itself over one thousand times into random spots in your computer
3) Hide its self and all other created files
4) Task kill MSN, Norton, Windows Explorer, Limewire.
5) Swap the left mouse button with the right one
6) Opens alert boxes
7) Changes the time to 12:00 and shuts down the computer
1) Copy itself into startup
2) Copy itself over one thousand times into random spots in your computer
3) Hide its self and all other created files
4) Task kill MSN, Norton, Windows Explorer, Limewire.
5) Swap the left mouse button with the right one
6) Opens alert boxes
7) Changes the time to 12:00 and shuts down the computer
Subscribe to:
Comments (Atom)